Zero Trust Security: A Journey, Not a Destination in IAM Cybersecurity
Evolving network landscapes have demonstrated that perimeter-based security architectures lack the finesse and control needed to defend against new threats, both internal and external, and a new security methodology is necessary.
As of 2024, 63% of organizations worldwide have fully or partially implemented a Zero Trust strategy, according to Gartner. However, most of these implementations cover only half or less of the organization’s environment and mitigate just 25% or less of enterprise risk. Despite this, 56% of security leaders say they’re adopting Zero Trust because it’s considered an industry best practice.
- How do you create Zero Trust Security?
- What is a zero trust approach?
- Which zero trust solution is right for your business?
- How to achieve zero trust cybersecurity?
We have developed this guide to answer these essential Zero Trust questions and more. From the benefits and challenges to creating a system design that grows Zero Trust, we’ll also demonstrate how to utilize the Zero Trust Security Model for future-forward, near-total protection against every attack vector.
Contents
Read straight through, or jump to the section you want to read
What is Zero Trust Security?
How to build Zero Trust Security with Reduced Trust
The Challenges of Zero Trust Security
4-Stage Zero Trust Security Assessment
How to implement Zero Trust Security in 6 steps
Zero Trust Security Webinars (On-Demand)
“The knock-on effect of a data breach can be devastating for a company. When customers start taking their business—and their money—elsewhere, that can be a real body blow.”
- Christopher Graham
UK Information Commissioner
What Is Zero Trust Security?
IT environments have become more fluid, open, and, ultimately, vulnerable. More companies are turning away from conventional methods such as VPN to keep their networks secure. Zero Trust is a security approach that addresses these new network realities by trusting no one.
The basic tenets of Zero Trust Security are:
- Trust nothing
- Secure everything
- Contextually authenticate requestors
- Contextually evaluate access requests
- Assess all requests
- Grant access by the Principle of Least Privilege (PoLP) or allowing users the minimum access privileges necessary to perform a specific job or task and nothing more
Traditionally, identity access management (IAM) and privileged access management (PAM) solutions have approached security as a closed and perimeter-based system.
Still, with growing networks of users, devices, and applications, threats are just as likely to come from within the boundary: internal threats can be as high as 50% depending on your industry.
Organizations have recognized the reality there are no longer any truly closed systems. Many migrate to Zero Trust to mitigate risk from cyberattacks from multiple entry points (including internal).
By 2025, more organizations are leaning into Zero Trust—not just as a buzzword, but as a necessary shift. Verizon’s 2025 Data Breach Investigations Report shows why: third-party involvement in breaches has doubled to 30%, and vulnerabilities in edge and VPN systems have jumped from 3% to 22%—an eightfold increase. Even with these risks, only 54% of vulnerabilities are patched within about a month. These numbers tell a clear story: traditional security models aren’t keeping up. That’s why more teams are turning to Zero Trust to protect what matters most—identity, access, and the systems that keep everything running.
Back to top
"As we’ve come to realize, the idea that security starts and ends with the purchase of a prepackaged firewall is simply misguided."
- Art Wittmann
Vice President, Business Technology Network
How to implement Zero Trust Security
We know many organizations are utilizing or planning to implement Zero Trust across their organizations. Zero Trust is the ultimate security goal, but getting there can take time.
A layered Reduced Trust approach provides essential stepping stones and is our recommendation for organizations on their way to Zero Trust.
This method can be implemented in any order, laying the groundwork to build your new Zero Trust paradigm. By focusing on these pillars of access management, many enterprise businesses have scaled their Zero Trust initiatives.
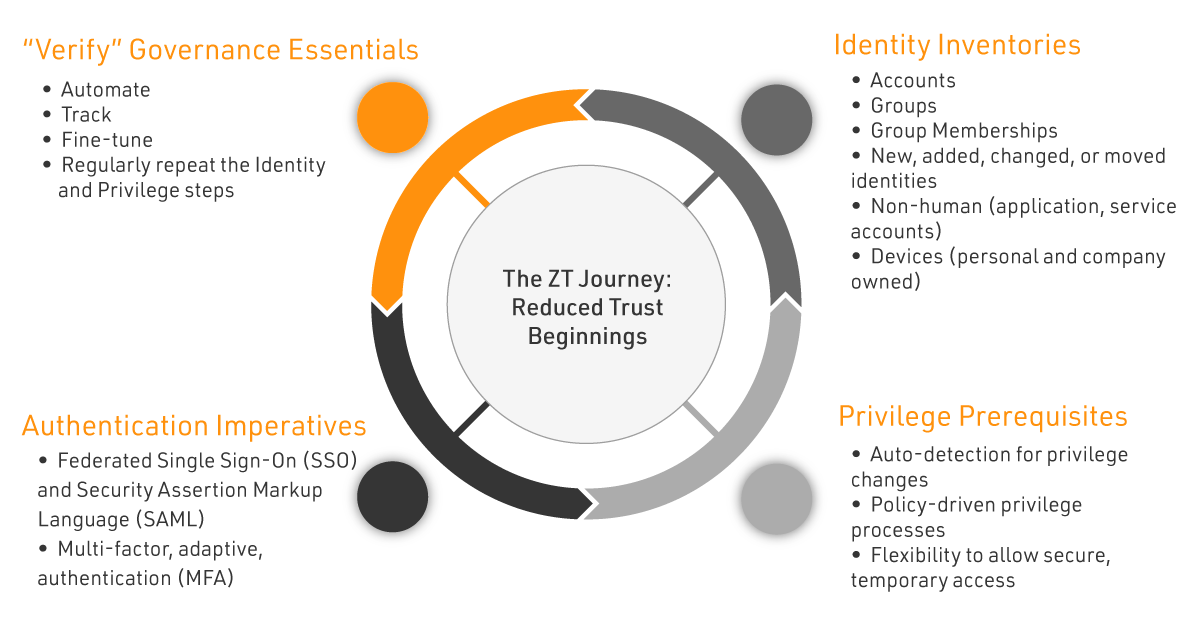
Identity Inventories
- Accounts
- Groups
- Group Memberships
- New, added, changed, or moved identities
- Non-human (application, service accounts)
- Devices (personal and company owned)
Authentication Imperatives
- Federated Single Sign-On (SSO) and Security Assertion Markup Language (SAML)
- Multi-factor, adaptive, authentication (MFA)
“Verify” Governance Essentials
- Automate
- Track
- Fine-tune
- Regularly repeat the Identity and Privilege steps
Privilege Prerequisites
- Auto-detection for privilege changes
- Policy-driven privilege processes
- Flexibility to allow secure, temporary access
Start Here
The Prerequisites
Organizations cannot begin their Zero Trust journey without these two critical steps to inventory what is in their networks:
Network Security & Inventory Audit
What businesses uncover in these processes will determine next steps.
Authentication
STEP 1: Ensure each application has its own security and access strategy for:
- Password management
- Federated authentication
- Randomizing administrative accounts
- Just in Time (JIT) access
STEP 2: Enable a federated authentication Zero Trust solution using a protocol such as SAML, OAuth, OpenID Connect, etc. (Security Assertion Markup Language).
STEP 3: Require additional verification, such as MFA Adaptive Authentication, for additional protection against internal and external threats.
Must-Haves:
- Federated SSO
- MFA
- SAML
- Adaptive
Governance
STEP 1: Implement dynamic security formulas to mitigate risk that may often include exceptions.
STEP 2: Minimize exceptions with automated policies, so only true outliers need additional management.
STEP 3: Track exceptions to monitor your organization’s overall risk trends and fine tune security policies.
Key Steps to Build “Never Trust, Always Verify” Governance:
- Automate
- Track
- Fine Tune
- Repeat Steps 2 and 3 Regularly
Privilege
STEP 1: Eliminate always-on access and privileges.
STEP 2: Enable policy-driven processes that minimize standing access and privileges while allowing for users who need temporary or shared account access.
STEP 3: Add account lifecycle automation to support zero standing privileges to reduce trust chains and overall risk.
Privilege Success Factors:
- Auto-detection for privilege changes
- Policy-driven privilege processes
- Flexibility to allow secure, temporary access
Identity
STEP 1: Create inventory of all identities to be brought into governance.
STEP 2: Review business processes.
STEP 3: Automate collection of entitlement information to significantly reduce the trust that would otherwise underpin your entitlement ecosystem.
Cover Your Assets:
- Accounts
- Groups
- Group Memberships
- Identities that are new, added, changed, or have moved
The Journey Continues ...
Reduced Trust, is a sustainable stepping stone you can achieve on your Zero Trust journey.
For continued success, you need a Zero Trust security model that leverages the investments you already have (ITSM, SIEM, OT, IoT, etc.) by seamlessly integrating them for both input and output.
BONUS
Zero Trust Worksheet
Embarking on a journey to build a zero-trust security model for your organization may feel daunting. Take the first step in planning your zero trust journey by using this worksheet to start a conversation with your stakeholders.
"We discovered in our research that insider threats are not viewed as seriously as external threats, like a cyber attack. But when companies had an insider threat, in general, they were much more costly than external incidents. This was largely because the insider that is smart has the skills to hide the crime, for months, for years, sometimes forever."
- Dr. Larry Ponemon
Chairman and Founder of the Ponemon Institute, a research “think tank” dedicated to advancing privacy, data protection and information security practices.
The Challenges of Zero Trust Security
Zero Trust is a program, not a project. While that may sound intimidating at first, you can approach it with small-but-actionable steps (like Reduced Trust) over a reasonable timeframe to achieve it at your own pace. Even so, there are some adversities you might encounter during your Zero Trust program.
Challenges Along Your Zero Trust Journey
Technical hurdles with legacy systems
Political challenges from admins over least privilege and loss of autonomy
Perceived friction in integrations across hybrid cloud, applications, devices, and more
Fear of change moving from silos to a data-centric model
Getting started with so many approaches, solutions, and implementations
What companies say:
“With 70+ systems to integrate, we need an adaptable API that can play nice with our complex environment.”
“We need professional services with a security solution that can be easily integrated into our environment and customized to our specific needs.”
“Moving from VPN to Zero Trust seems like an impossible task when I am not even sure my legacy system is compatible with least privilege.”
“Access management security solutions require so many vendors and program deployments. It can be costly, time-consuming, and hard to manage!”

Can you overcome these challenges by yourself?
It is possible — but it requires proper implementations, skill sets, time, and budget.
But what if there was an easier way? Explore solution >
"The health sector continuously get’s pummeled by malicious actors and hackers because their cyber-kinetic security is being managed by “Participation Trophy” winning wimps!"
- James Scott
Senior Fellow, Institute for Critical Infrastructure Technology
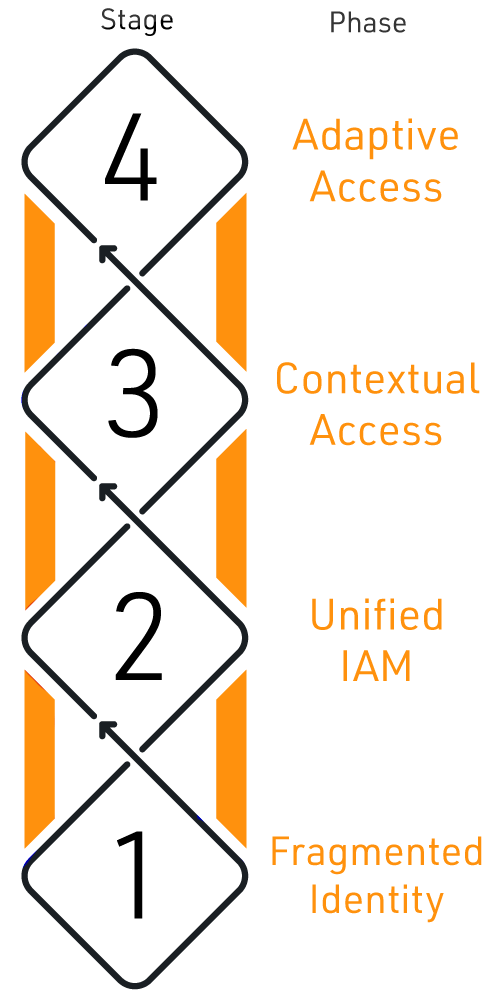
4-Stage Zero Trust Security Assessment
This four-stage Zero Trust maturity pre-assessment will help you identify what stage your organization is in on a journey towards operational Zero Trust Security alignment.
STAGE 1 : Fragmented Identity
- High reliance on the perimeter
- Active directory on-premises
- No cloud integration
- Passwords wherever
STAGE 2 : Unified IAM
- Single sign-on across employees, contractors, and partners
- Contemporary multi-factor authentication
- Cooperative policies across applications and servers
- Vaulting and randomizing of privileged accounts
STAGE 3 : Contextual Access
- Context-based access policies
- Automated joiner/mover/leaver processes de-provisioning for those leaving
- Group Management
- Multiple factors deployed across users
- Secure access to APIs
- Safeguarding services, non-human accounts, containers
STAGE 4 : Adaptive Access
- Risk-based access guidelines
- Adaptive and continuous authorization and authentication
- Frictionless access
- Diminished emphasis on the perimeter
- Just-In-Time (JIT) access
- Centralized provisioning
Remember
Zero Trust is a journey, not a destination. You can take each step at your own pace as you progress toward maturity.
Learn how we can help you get there faster. Explore solution >
"Let’s face it: the future is now. We are already living in a cyber society, so we need to stop ignoring it or pretending that is not affecting us."
- Marco Ciappelli
Co-Founder of ITSP magazine
How to implement Zero Trust Security in 6 steps
This six-step Zero Trust Maturity Model (ZTMM) is adaptable and proven to help you advance toward your new IAM and PAM standard. Start discovering the benefits of a singular, powerful, and layered solution for your evolving Zero Trust paradigm with this strategy.
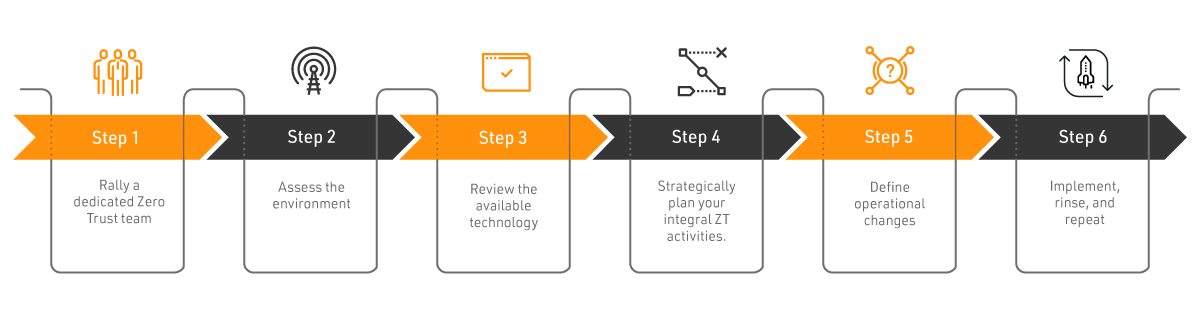
STEP 1 : Rally a dedicated Zero Trust team.
Zero Trust is one of the most transformative actions that an organization can undertake. You may be tempted to cast a wide net by making Zero Trust an organization-wide strategic initiative, but this can make it less imperative and slow the process as a task that ranks below everyone’s top to-dos.
Instead, elect a small team tasked to plan and implement your Zero Trust migration. This team should Include internal members from:
- Applications and data security
- Network and infrastructure security
- User and device identity
Remember
Your Zero Trust Security initiatives must have full sponsorship. Leadership and stakeholder support are crucial.
Learn how we can help guide you there. Explore solution >
STEP 2 : Assess the environment.
Taking an inventory of all devices that access your network is critical, even if you may not be able to compile a fully comprehensive and complete view of your infrastructure. Your inventory should include devices owned by your organization and those that are not. Moreover, simply cataloging this information is not enough; you must understand these devices’ security status and the controls around them as well.
In addition to devices, your organization should also look beyond hardware across resources to software and users, including:
- Accounts
- Groups and group memberships
- New, added, changed, or moved identities
- Non-human (application and service accounts)
- Virtual machines and containers
STEP 3 : Review the available technology.
The National Institute of Standards and Technology (NIST) identifies three main approaches to implementing a Zero Trust Architecture (ZTA):
While each of these methods carries its strengths and is not mutually exclusive, at Bravura Security, we believe that highly automated IAM offers one of the most expedient and cost-effective ways to launch your Zero Trust journey.
Remember
A comprehensive Zero Trust program requires participation from multiple departments within your organization.
Occasionally, this may result in political friction that can be deflected when planning and direction originate outside the organization.
Learn how we can help guide you there. Explore solution >
STEP 4 : Strategically plan your integral Zero Trust Security activities.
Security Fabric Framework
As no two organizations are the same, we recommend adopting this structure as a planning aide for your Zero Trust program:
- Start with multi-factor, adaptive authentication, and single sign-on (SSO)
With a trending resurgence of de-perimeterization, it’s easy to see the benefits of these implementations early in the process in a world where software-as-a-service (SaaS) adoption by a remote workforce is increasingly prevalent.
- Move to privileged access
In light of recent headlines and strong regulatory obligations, this step is also an early necessity. Hackers are not breaking in--they’re logging in, finding ways to move laterally, and elevate access. Vaulting and randomizing passwords for highly privileged accounts is an effective deterrent against such tactics.
- Build out your identity fabric patchwork, which ideally consists of a set of components like microservices and containers; beyond essential services, other pieces may be necessary to your organization, including:
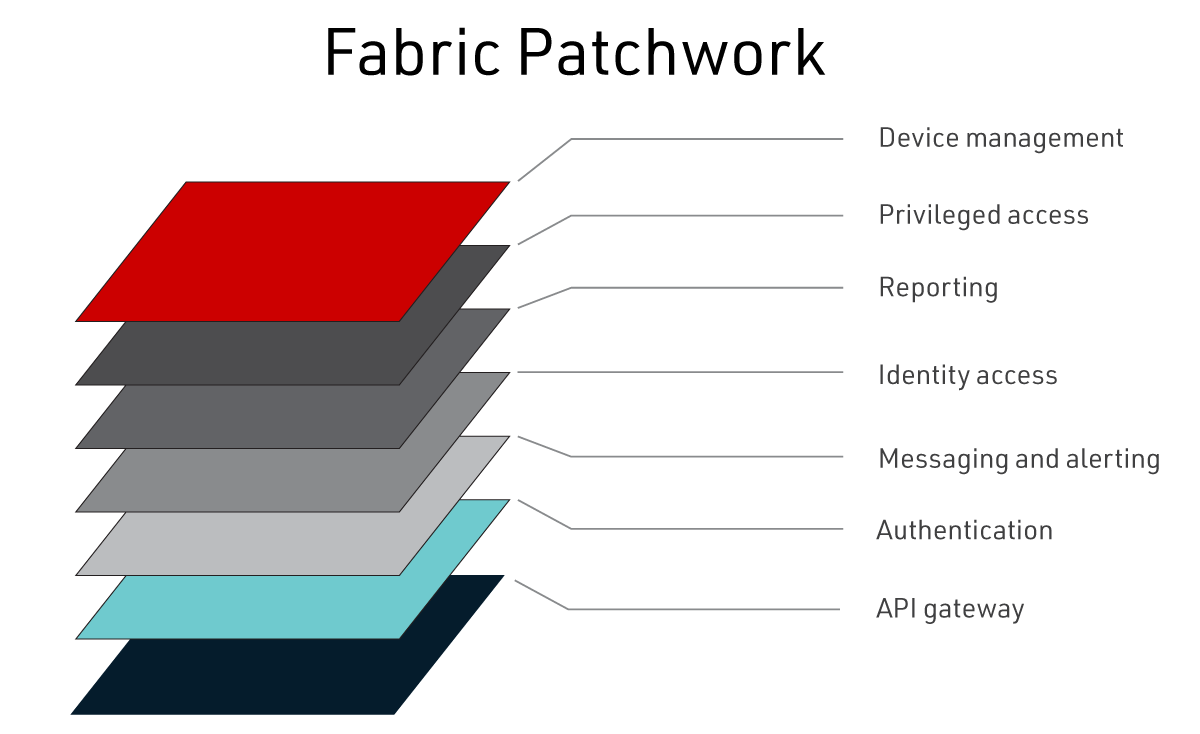
- Leverage this Security Fabric Framework
This methodology is versatile, collaborative, and driven by use cases, business needs. Furthermore, it establishes your ZTA as a program, not a project with tightly-knit components.
Remember
As you complete each project in your Zero Trust program, revisit the Security Fabric Framework with your team
and reevaluate objectives, fire drills, and threat modeling.
Learn how we can help guide you there. Explore solution >
STEP 5 : Define operational changes.
Zero Trust strategy can fundamentally change security operations. For example, as tasks are automated, corresponding manual tasks might need to be modified or automated to keep pace and prevent security gaps. Disciplined change management practices will be important as each piece of the fabric gets stitched together, and the next steps take form.
STEP 6 : Implement, rinse, and repeat.
As your organization deploys new technologies, assess their value according to security key performance indicators (KPIs), including the average total time to contain incidents, which should decrease dramatically the closer an organization moves to Zero Trust.
Back to top"It takes 20 years to build a reputation and few minutes of cyber-incident to ruin it."
- Stephane Nappo
Global Head Information Security
Introducing Bravura Security Fabric
Bravura Security Fabric delivers an enterprise-grade solution to identity protection, built-in threat detection, and a singular identity, privileged access, and password platform. This all-in-one platform will bring absolute focus to implementing your Zero Trust approach.
The Bravura Security Fabric is truly cloud, platform, and security system agnostic. It’s a single open architecture platform and the industry’s most extensive organically grown connector portfolio. Bravura Security Fabric offers a robust API platform to complete your security strategy — integrating natively with other security systems and implementations at whatever stage of your enterprise Zero Trust journey.
Singular, Powerful, and Layered. That’s Bravura Security Fabric.
The fabric creates a centralized view to weave the patterns of functionality your organization needs to protect against continual threats and cover all aspects of your identity and access security program. As you uncover new identity and access threats or your roadmap evolves, simply turn services on or off as needed. Improve IT security, support internal controls and regulatory compliance, and lower administration and costs — all without installing other products.
Bravura Security Fabric meets all of your digital identity and access security needs with industry-leading features and applications enterprises require. It’s packed with future-ready technological and architectural building blocks enhanced by decades of reliability to protect, manage, and govern your entire identity and access infrastructure for the next generation. All of this scalable capability comes bundled with Bravura Security’s global support.
Did You Know
Bravura Security Fabric integrates with the latest security tools, including:
- the Internet of Things (IoT)
- Operational Technology (OT)
- Information Technology Service Management (ITSM)
- Security Information and Event Management (SIEM)
Zero Trust Benefits
Bravura Security Fabric
- solves the latest, evolving access management challenges
- delivers the solution with the industry’s only single platform for multi-factor, adaptive authentication, IAM, and PAM
Integrative
Leverage the industry’s most extensive organically grown ecosystem connector portfolio with seamless two-way integrations, offering a robust API platform to complete your security strategy
Combine freely utilizing the open architecture solution empowered by genuine agnostic integration support for all security platforms, implementations, and Zero Trust targets
Uncover more with Bravura Discover, which allows you to assess threats and risks across systems, improving your response time and making your Zero Trust strategy more exhaustive
Customizable
Weave and apply parts of the fabric to your journey over time as you uncover unknown threats, and your roadmap evolves
Use optional automation and detection, governance and compliance, and analytics and reporting. Turn services on or off as needed without installing other products
Manage your access management and integrations — no matter what service created them
Comprehensive
Access one platform and framework that brings together all layers of Bravura Security Fabric, including Identity, Privilege, Pass, and Group plus a threat detection layer: Bravura Discover
Gain visibility and threat intelligence around your entire ecosystem
Work in partnership with to create a comprehensive program that addresses your specific needs our global support helping you meet challenges at every step of the way
Back to topZero Trust Security Webinars
Top Cybersecurity Outcomes a Zero Trust Model Delivers
Organizations turning to zero trust security models to protect their resources and data are realizing substantial business benefits and outcomes. Learn more on June 24
Watch NowThe Zero Trust Journey with Identity and Privileged Access Management
Zero trust and legacy workflows can coexist as you tackle one business process at a time as your organization enhances operational maturity and cybersecurity resilience.
Watch NowPlanning Your Zero Trust Journey With Enhanced Identity Governance
Embarking on a journey to build a zero trust security model for your organization may feel daunting. But there are actionable steps you can take to get started.
Watch NowProtecting Your Privileged Access in a Zero Trust Security Model
Gain practical insight into how to implement controls that establish and maintain contextual, adaptive trust to protect privileged access.
Watch NowZero Trust Blog Posts
Expert Zero Trust Paths 2025: IAM, SDP & Segmentation
Today, there are several ways your organization can implement a Zero Trust Architecture (ZTA). Each method varies in its components and organizational policy rules, resulting in a distinct architecture. The National Institute of Standards and ...
Read MoreThe Zero Trust Security Model Companies Need Now
In the last two years, 79% of organizations have experienced an identity-related security breach, according to research from the Identity Defined Security Alliance (IDSA). That’s a truly staggering number, however, the even more shocking statistic ...
Read MoreWhat Is the Difference Between PAM, PIM and PUM?
When it comes to managing restricted access within an organization’s IT and digital assets, systems administrators have many factors to consider when granting privileges. IT decision-makers need to prioritize cybersecurity while also providing a way ...
Read More





