Contents
Read straight through, or jump to the section you want to read
What is Identity Governance and Administration?
Why is Identity Governance important?
What Is Access Management?
How to Build a Business Case for an Identity Governance Solution
Access Management Challenges
Why you need a Zero Trust Program
Why Your Vendor Matters
Introducing Bravura Security Fabric
63%
of breaches involved weak, default or stolen credentials.
Source: Verizon Databreach Report
What Is Identity Governance and Administration?
Identity governance and administration (IGA) systems, sometimes also called user provisioning, access governance or identity and access management (IAM) systems, externalize the management of users, identity attributes and security entitlements out of individual systems and applications into a shared infrastructure.
Identity governance and administration tools make the creation, management and deactivation of login accounts, home directories, mail folders and security entitlements faster, less costly and more reliable. Modern IGA is done by automating business processes for onboarding, change requests and deactivation for each user community and by linking these processes to the systems and applications that have account repositories.
Identity governance and administration systems generally implement one or more of the following processes:
- Automation:
Detect adds, changes and deletions in a system of record (SoR, such as HR) and make matching changes – create accounts, grant/revoke access, etc. on integrated systems and applications. - Self-service requests:
Enable users to update their own profiles (e.g., new home phone number) and to request new entitlements (e.g., access to an application or folder). - Delegated administration:
Enable managers, application owners and other stakeholders to request changes to identities and entitlements within their scope of authority. - Access certification:
Periodically invite managers and application or data owners to review users and security entitlements within their scope of authority, flagging inappropriate entries for removal. - Identity synchronization:
Detect changes to attributes, such as phone numbers or department codes on one system and automatically copy to others. - Authorization workflow:
Validate all proposed changes, regardless of their origin and invite business stakeholders to approve them before they are committed.
Identity governance and administration platforms generate value by applying the identity and entitlement changes produced by the above processes to account repositories, using connectors that can:
- List existing accounts and groups.
- Create new and delete existing accounts or groups.
- Read and write account or group attributes.
- Read and set flags, such as “account enabled/disabled,” “account locked,” “intruder lockout” or “group type.”
- Change the login ID of an existing account (rename user).
- Read an account’s groups or a group’s members.
- Add accounts to or remove accounts from groups.
- Add child groups to or remove child groups from parent groups.
- Move accounts between directory organizational units (OUs).
Back to top
Primary Goals and Functions of IGA Solutions
A complete identity governance and access management solution aims to create:
- More visibility: Transparency into user identity and access lets you identify and remediate potential risks sooner.
- Enhanced data and system protection: When you combine accurate provisioning and credentialing with high-level account access controls, you get better protection for business resources.
- Improved compliance and enforcement: IGA tools make auditing, regulatory compliance and policy enforcement easier through tracking and accountability.
Did you know?
In 2020, breaches at Marriott Hotels and MGM Resorts exposed the personal information of close to 16 million guests. The data was later shared on a popular hacking forum.
Why Is Identity Governance and Administration Important?
The digital disruptions of the pandemic have further emphasized the need to stay current with technology. The risk? Falling behind others who have embraced the acceleration of digital transformation and future-facing IT strategies in the face of hybrid learning futures.
Access management modernization reduces risk (and the risk accompanying new technology implementations) with digital identity accountability, security and optimization processes with automation. Most organizations cannot make the business case to invest in IAM without it being the precursor to the implementation of technology with more obvious user benefit and ROI. So, without powerful IAM and privileged access management (PAM) implementations, which deliver these crucial modernization competencies, you risk compromising your whole modernization strategy.
The roadmap to support a comprehensive and cohesive access management culture isn't always straightforward. And many don't know where to start. How do you create an access management culture that cultivates your modernization strategy? What platforms, processes and technologies meet your unique access needs?
We have created this guide to help you discern the processes and technology to support digital transformation and more. From defining identity access management, privileged access management, IGA platforms and cyberattack solutions to achievable steps, unique challenges and universal benefits, we'll provide a blueprint for creating your access management digital strategy and transformation.
Back to top
82%
of breaches happened within minutes.
Source: Verizon Databreach Report
What Is Access Management? Why Your Platform Matters
Few IT leaders would argue against access management’s critical importance. Access management refers to the processes and technologies used to control and monitor network access.
Most organizations using legacy tools and homegrown solutions face significant challenges. These open-source and custom systems haven't aged well because there isn't an incentive to innovate them. They're highly manual and labor intensive, and many weren't built with security in mind — leaving them expensive to maintain, enhance or fix.
It's time for an upgrade.
Your access management process and technology, including identity access management and privileged access management, are crucial components of a digital strategy that must be replaced or modernized to remain viable. The problem is many platforms are not designed for every industry, and many vendors are unfamiliar with these unique obstacles.
Plus, an ad-hoc, custom-coded and reworked solution can be a very costly, time-consuming and complicated approach.
Back to top
Did you know?
In 2021, Colonial Pipeline Co., a very large East Coast gas utility, suffered a ransomware attack that shut down the company for six days, along with Facebook and Volkswagen due to breaches.
How to Build a Business Case for an Identity Governance Solution
We recognize many may not have the budget or ability to tackle complete access management programs that include IAM, PAM and IGA. You may need to start small with high-impact projects that will get you the best ROI. These bite-sized achievable tasks will help you steadily piece together the access management digital transformation puzzle.
After performing a prerequisite inventory (illustrated below), you can complete these initiatives in any order, but each little project will help you build a new access management model and begin your efforts around a comprehensive authentication and identity program. By tackling segments of both, you will create a foundation for future 360-degree access management success.
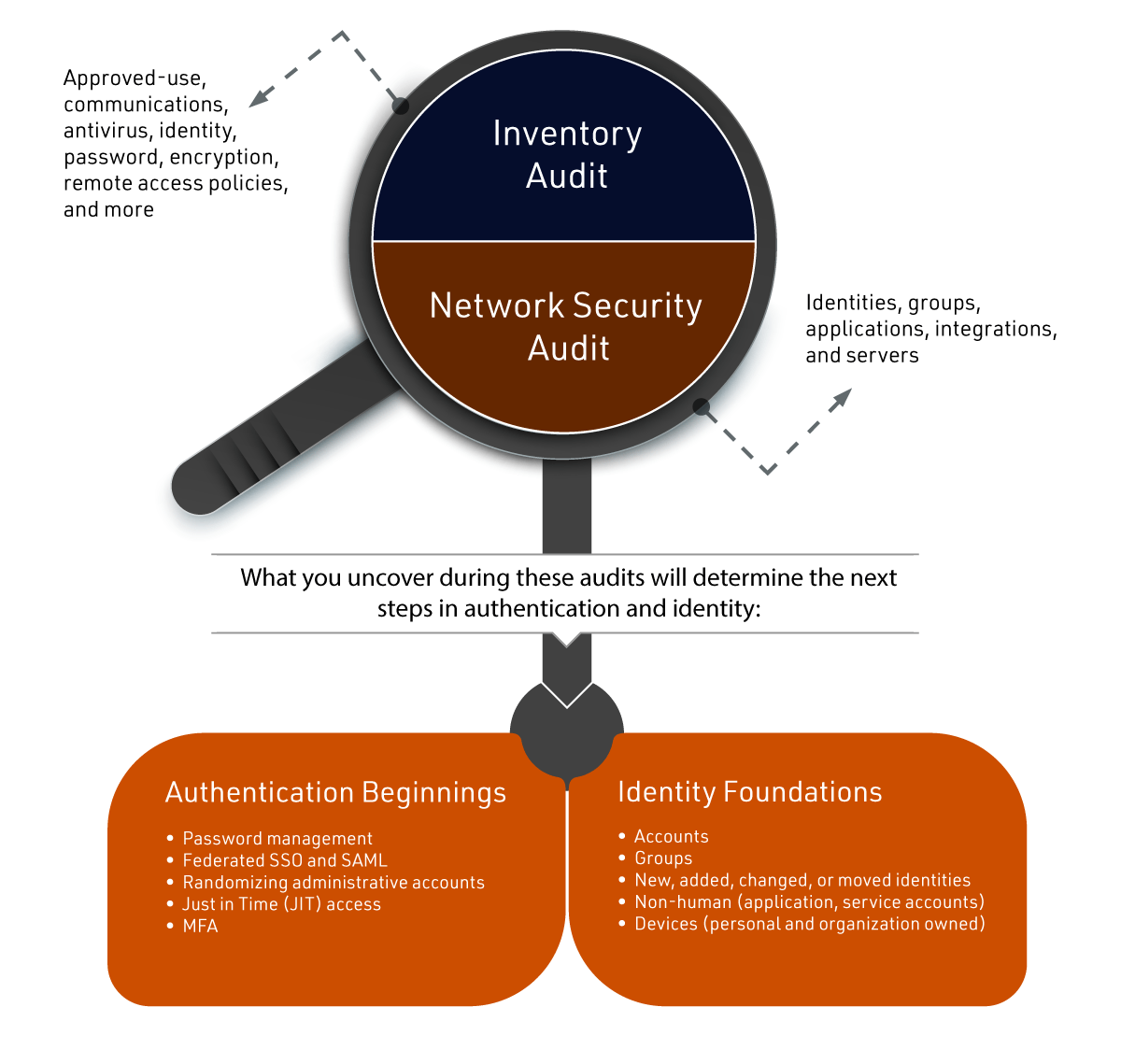
Prerequisite Inventory
Before executing your access management digital strategy, take stock of what’s in your network:
Inventory Audit
- Approved-use
- Communications
- Antivirus
- Identity
- Password
- Encryption
- Remote access policies
Network Security Audit
- Identities
- Groups
- Applications
- Integrations
- Servers
What you uncover during these audits will determine the next steps in authentication and identity:
Authentication Beginnings
- Password management
- Federated single sign-on (SSO) and Security Assertion Markup Language (SAML)
- Randomizing administrative accounts
- Just-in-Time (JIT) access
- Multifactor authentication (MFA)
Identity Foundations
- Accounts
- Groups
- New, added, changed or moved identities
- Non-human (application, service accounts)
- Devices (personal and organization owned)
You can “start small” with viable and high-yielding ROI projects utilizing these flexible mile markers. To help you overcome a common roadblock many often face in gaining decision-maker support. Many leaders need a path that resonates with them before they will greenlight a modernization project.
95%
of confirmed web app breaches were financially motivated.
Source: Verizon Databreach Report
Access Management Challenges
Organizations face unique access management challenges. However, by creating the right access management processes and pairing them with a properly designed solution that includes IAM and PAM, your organization can handle many of these challenges. The best part? You will reclaim hundreds of hours for your IT leadership to spend on more strategic projects.
Top challenges with access management:
1. Getting Started
The first step is always the hardest, and for organizations working to implement a new IAM solution, it's a steep uphill climb. Building support among decision-makers continues to be difficult for most, making it challenging to move forward with IAM, IGA and identity administration projects. It's a daunting task, to say the least, but with the right approach, you can get your IAM programs up and running.
Starting small with introductory projects (i.e. begin automation to clean up credentials and identities) can help build some momentum. It will also give your IT team some use cases to put in front of leadership and hopefully inspire confidence to further invest in these initiatives. Implementing these new solutions and processes will take time, but with flexibility and perseverance you can get started on the road to stronger identity and access management.
2. Aging Homegrown and Legacy Systems
Many companies are often saddled with legacy and homegrown solutions they have been using for years, on account of limited and constrained budgets (along with siloed structures and processes). While these systems may have met the organization's needs at one time, they have grown inefficient over time and prone to increasing human error. All too often, the mastery of these systems is concentrated among one person or a small group of people due to their DIY nature. If or when that person leaves, another vulnerability is created.
To combat risk and reclaim hours, you need to prioritize updating legacy access management systems and processes. With a digital transformation strategy focused on a singular approach to bring all of the critical actions of access, identity, and privilege together, you will be better equipped to manage access and reduce the risk of unauthorized entry.
3. Blended Roles and Non-Hierarchical Structures
It’s not uncommon for someone in a company to take on several different roles simultaneously. And when you include external access, it is common for many users to maintain many more than two roles. Privileged access systems are versatile enough to support these multi-role requirements, preventing potential exposure of confidential information while simultaneously protecting the organization’s cybersecurity.
Decentralized architecture with frequently disparate systems is also a hurdle. Each department within an organization may have a unique structure, creating obstacles when aligning individual departments with the overarching systems. Identities may not match up, or appropriate access can be incorrectly granted or blocked. A robust IAM and identity governance solution (paired with access management best practices) can organize and automate these contrasting frameworks, minimizing misappropriation and maximizing interdepartmental access alignment.
These hybrid roles can present another challenge for the segregation of duties (SoD). With a robust separation of duties policy, no individual user can conduct an end-to-end transaction without the proper checks and balances in place. These strategies help reduce the risk of fraud and human error. A full-featured IGA solution can help with tools like contextual risk-based access review, identity-level visibility and control, and real-time alerts.
4. Dynamic User, Granular Permissions and Staff Populations
For organizations with heavy turnover, the onboarding and offboarding of large numbers of users presents an even higher risk. Some users may even have levels of access beyond the typical user case, which makes automatic offboarding crucial to maintaining the security and integrity of your system.
This active, overlapping and manual process is rife with human error and misappropriated accounts and profiles. It can also be time-consuming and cause delays in onboarding, sapping valuable time and limited bandwidth from IT staff and leadership. And when the process breaks down, it creates orphaned, dormant and stray accounts that increase risk and vulnerability to bad actors if left unchecked.
An access management solution, including IAM, identity governance, and PAM, automates and augments this process by strengthening governance and reducing vulnerability. An access management implementation cuts down on the number of inappropriate access rights and lost accounts by introducing automatic access deactivation and control processes.
Lastly, by automating these time-consuming tasks, companies make IAM and identity administration processes more efficient, optimizing their team, improving the users connection with the company, and, ultimately, freeing them up for more innovative projects.
Back to top
“IAM challenges have become increasingly complex, and many organizations lack the skills and resources to manage effectively. Leaders must improve their approaches to identity proofing, develop stronger vendor management skills and mitigate the risks of an increasingly remote workforce.”
Akif Khan, Senior Director Analyst, Gartner
Why You Need a Zero Trust Program
Zero Trust is a program, not a project. While that may sound intimidating at first, you can approach it with small but actionable steps (like Reduced Trust) over a reasonable timeframe to achieve it at your own pace. Even so, there are some adversities you might encounter during your Zero Trust program.
Access Management Responds to Rapid Change
Growing Cyberattacks
According to Verizon's 2020 data breach report, there were a total of 32,002 reported incidents and 3,950 breaches with confirmed data disclosure. With the rise in remote access, it's clear organizations will continue to face increased risks as more organizations move to software as a service (SaaS) applications.
Organizations can protect themselves against threats by staying a step ahead with IAM (including identity governance) and PAM. In an environment without access management and expected risk, many cybersecurity strategies involve damage control from exposure. By removing many manual tasks and static passwords, you can shift cybersecurity strategies from reactive to proactive.
Another step can be taken forward by adding predictive analytics and technology. These powerful tools, at the heart of cutting-edge access management solutions, can anticipate and forecast complications before they are exploited. Organizations can then further fortify these efforts with risk and threat assessment, plus resolution recommendations, completely moving away from reactive to proactive strategies toward risk.
Evolving Regulations and Compliance Requirements
Many organizations spend a lot of time and money on certification and governance initiatives, but without automation measures in effect, their compliant state will not last. IAM automation and identity administration strategies ensure rights are assigned and removed promptly, maintaining compliance without the need for manual interventions. Modern systems also automate the role review process and provide access for auditors, saving many hours of reporting and study.
Predictive analysis of users’ needs will then help reduce the number of generated requests, and an efficient workflow engine at the center of access management solutions guarantees those requiring approval are provisioned on time.
Zero Trust
The future of cybersecurity is the Zero Trust model as IT environments have become more fluid, open and vulnerable. More organizations are turning away from conventional methods such as virtual private network (VPN) to keep their networks secure, with many implementing Zero Trust — a security approach that addresses these new network realities by trusting no one.
While some companies may not yet be able to sprint toward Zero Trust architecture, taking crucial first steps, like network and inventory audits, can lay the foundation for success. Investing in IAM and PAM solutions that enable strong integration (for input and output) will allow an organization to scale more efficiently, add tools and features and implement initiatives like Zero Trust when they're ready.
Modernization and Optimal Experience
As more organizations embrace digital ecosystems, access management processes and technology can guide your digital strategy. IAM and PAM implementation creates a methodology across authentication, identity, privilege and “verify” governance. This practice lays the groundwork for comprehensive and secure modernization.
The winning combination also creates access management synergy and an optimal experience for all types of users where IAM creates identity and PAM secures it. As you move further into modernization, this hybrid 360-degree approach is required to remain competitive in the modern landscape we are in.
Want to learn more about Zero Trust?
Read our comprehensive Zero Trust Guide
Why Your Vendor Matters
You have a choice when it comes to choosing an access management solutions vendor that meets all of your organizations needs.
The problem: While many modern IAM and PAM options are available, few are customizable and versatile enough to meet those challenges (both micro and macro) without making compromises along the way.
You need a vendor that will be with you throughout your journey — a relationship with an experienced team can help you select and sequence your IAM, identity governance, PAM implementations and more. At each phase, they should work with you to ensure smooth execution and performance.
The right partner can help you make critical strategy decisions that move your access management culture beyond legacy systems and ever-forward. A vendor with extensive experience can help you avoid project pitfalls specific to your organization.
Back to top
-7.27%
is the average percentage share prices fall after a breach
Source: Comparitech
Introducing Bravura Security Fabric
Bravura Security Fabric delivers a cutting-edge solution to identity protection, built-in threat detection, singular identity, privileged access and password platform. This all-in-one platform is ready-made for organizations — conquering access challenges out of the box without expensive customization.
Modern IGA challenges need technologically advanced and easy-to-use IGA solutions. Truly framework agnostic, Bravura Security Fabric integrates across various cloud, platform and security systems with versatility and adaptability. It automates the complex life cycle management of large, dynamic and unusual user bases — without the need for ad-hoc scripting or additional resources and staff.
The Only Platform That Manages Identities With ONE Powerful Solution
The Bravura Security Fabric singular, powerful framework and platform brings together all the layers of Bravura Security:
Bravura Identity
Get robust digital proxy management with Bravura Identity. Use this functionality to:
- Create and manage identities over their organizational life spans.
- Modify access and implement least privilege controls.
- Reduce IT team decision-making through provision and deprovision with intelligent automation.
Bravura Privilege
Protect high-level data with Bravura Privilege. This component of our complete identity and access governance platform lets you:
- Initiate application sessions with shielded credentials from an encrypted vault.
- Trace privileged data access for compliance and accountability.
- Randomize complex passwords to harden data security.
Bravura Pass
Simplify password management and improve the end user experience with Bravura Pass. These tools offer:
- Strong authentication: We've built in the option to use biometrics as an identity challenge.
- Self-serve user tools: Password and PIN resets are user-initiated and automated for fewer IT support requests and higher productivity.
- Single sign-on support: Bravura Pass includes functionality to launch applications from within the dashboard with password synchronization capabilities.
Bravura Safe
Put passwords your employees use every day for internal and external resources in one encrypted vault. Bravura Safe provides:
- Complete visibility — minus the passwords themselves — to your IT security team for each resource.
- Convenient one-password access to employees to the platform with unified identity management across their devices.
- An encrypted vault for password storage of currently decentralized sign-on information.
- Automatic password generation for strong and unique passwords to each access resource.
Bravura OneAuth
Go passwordless and boost user satisfaction while ensuring speed and security. Bravura OneAuth supports:
- MFA via mobile app or biometric identifiers.
- Fewer IT support tickets for password reset requests.
- Up to 300% time savings in authentication processes.
- Phishing resistance with a proven track record.
Benefits
Bravura Security Fabric meets all of your digital identity and access security needs with industry-leading features and applications. It's packed with future-ready technological and architectural building blocks enhanced by decades of reliability to protect, manage and govern your entire identity and access infrastructure for the next generation. All of this scalable capability comes bundled with Bravura Security's global support.
Implement a singular platform designed for IAM (including identity governance administration) and PAM challenges out of the box without expensive customization.
Simplify your vendor and program deployment, streamline service-level agreements and lower overall cost.
Address your most urgent PAM, MFA and federated SSO needs with the ability to enable services as you need them.
See value faster while it evolves to protect institutional research, data, finances and reputation from cybersecurity threats.
Seamless integration: The solution also integrates with the latest security tools, including the Internet of Things (IoT), Operational Technology (OT), Information Technology Service Management (ITSM) and Security Information and Event Management (SIEM).
Bravura Security Fabric as a Cloud-Based Solution
Bravura Security Fabric is also available as a cloud-based SaaS solution. Benefits of our cloud identity governance platform include:
Scalability: Add or retire credentials and enable services as you need them.
Affordability: Limit your initial infrastructure spending — our cloud identity and access governance tool runs using servers we maintain.
Accessibility: Get access to the platform from any connected device, secured by multifactor authentication and robust endpoint risk analysis.
Explore Our Technology With a Free Demo
Take an in-depth look at our platform to see how the power of one solution transforms identity and access management governance.
Request a demo to get started.
Interested in Learning More About Our Solutions?
Our software automates processes to securely and efficiently manage identities, entitlements and credentials. Bravura Security solutions help organizations lower IT operating costs, improve user service and strengthen security.
Learn More