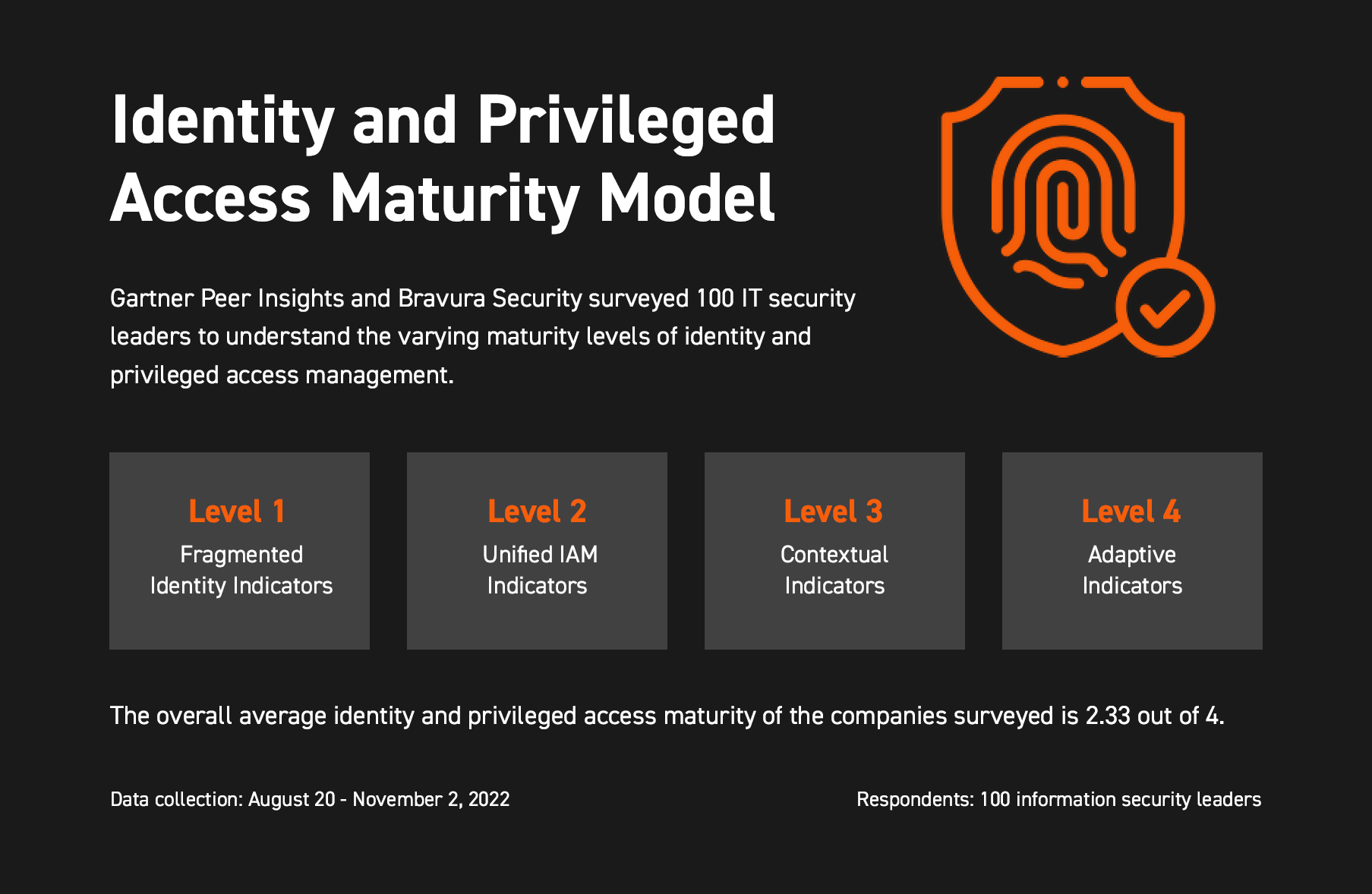
Identity and Privileged Access Maturity Model [Survey Results]
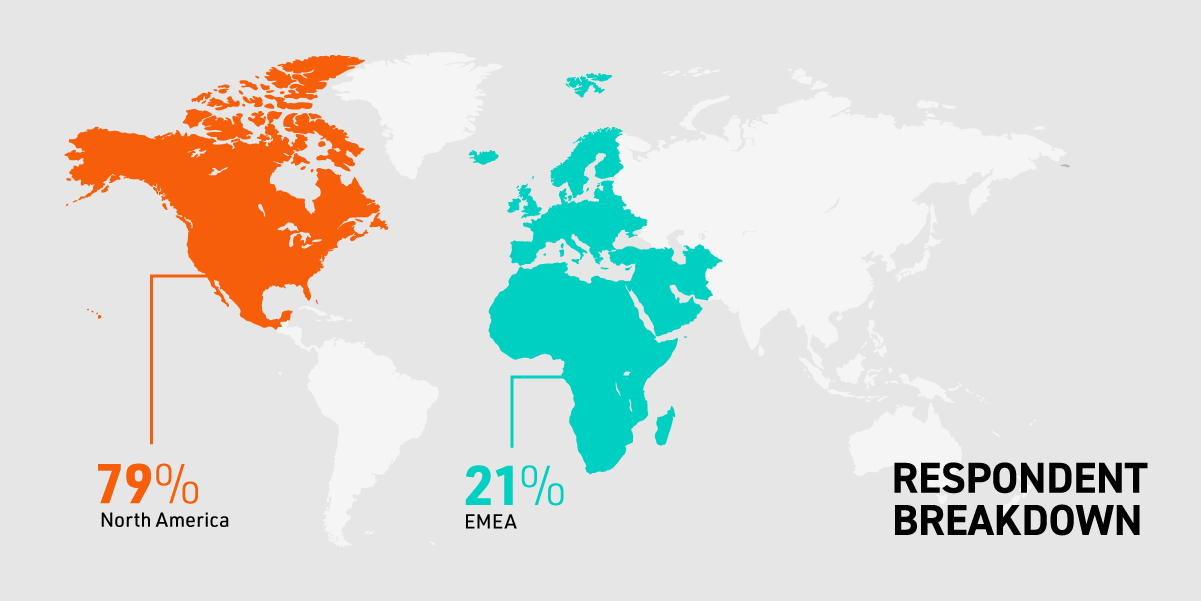
We partnered with Gartner Peer Insights to get a deeper look at where organizations are in their identity and privileged access management journeys. The survey included 100 IT leaders at organizations of varying sizes from North America, Europe, the Middle East and Africa (EMEA).Our study measured respondents' maturity levels in various Identity and Access Management (IAM) and Privileged Access Management (PAM) processes. What we found in the IT IAM maturity survey results may surprise you.
The Bravura Security IAM & PAM Program Maturity Model
We scored our respondents' maturity levels on a scale of one to four, with four being the most mature:
- Fragmented identity: IAM controls are either nonexistent or disparate across the environment, potentially opening the organization up to unnecessary risk.
- Unified identity: The organization uses a unified system with a single source of truth for most — if not all — applications.
- Contextual identity: The system uses context indicators, like geographic location and user behavior, to automatically adjust access controls.
- Adaptive identity: The system is highly dynamic and automated, enabling it to respond to new threats quickly without input from human users.
The average maturity score was between two and three, indicating that there's still room to grow for most organizations. Let's explore some of the biggest factors in identity and access management maturity.

%20(1)-resize.png)
Contents
Read straight through, or jump to the section you want to read
Access Management and Authentication
Promising Signs in Identity Management and Administration
Most Organizations Focus on Multi-Factor Authentication (MFA)
More Than Half Leverage Privileged Access Management
Role-Based Access Control (RBAC)
Many Businesses Automate Life Cycle Management
Most Organizations Are Lagging Behind on Governance
Download Infographic
Access Management and Authentication
Access management includes the processes and technologies that allow your organization to grant and manage access to all applications and systems within your IT network. It's essential for protecting your resources from unauthorized access, which is why consistency is key.
Incorporating automated technology into access management processes is an excellent tool for applying consistent policies across all your applications. There are a wide range of factors that go into an organization's access management maturity, including authentication methods and access control strategies.
Promising Signs in Identity Management and Administration
Identity access management is a cybersecurity framework for managing what each individual user can access within your network. It's a critical consideration for protecting sensitive data, as it restricts access to certain resources based on each user's need. In our survey, we found that the average IAM maturity score was 2.33 out of four.
Nearly two-thirds (64%) of respondents said their organization had a primary directory that served as their single source of truth for most — if not all — of their internal identities. Identities from other systems could link back to this directory, which provided mostly consistent data across the system.
Although another 24% used the primary directory as their only source of network authority, 12% used various sources of truth for identity information, which caused fragmented data. Without a centralized source of truth, properly managing identities across your organization is difficult at best and near impossible at worst.
Back to topMost Organizations Focus on Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) requires users to provide multiple identifying factors in order to log in. It's significantly more secure than your standard username-password combination, but it has its limitations.
MFA fatigue, for example, is a growing problem. Attackers can steal usernames and passwords, but they can't remotely respond to a push notification on someone else's smartphone. So they spam the victim with notifications until they accidentally grant access to their account. Finding ways to eliminate this problem, such as passwordless security, is going to be crucial in the coming years.
In our survey, we discovered that 95% of organizations have implemented some level of MFA in their environments with varying degrees of standardization. And 11% were able to create a frictionless experience using dynamic, contextual policies that reduce MFA fatigue.
Back to topMore Than Half Leverage Privileged Access Management
Privileged access management is a specific IAM approach that grants and revokes elevated access as needed to reduce the risk of data loss. There are many technologies and policies that go into a comprehensive PAM solution, including password vaults and just-in-time approaches.
Our survey found that 56% of organizations store all their shared credentials — such as super-administrative credentials — in an enterprise-wide vault. Organizations in this group also leveraged basic vault integrations such as automated audit and account rotation, which helps keep credentials from being abused. However, these organizations could stand to use more advanced controls.
Only 6% used a Just-In-Time (JIT) approach — granting privileges only when needed — to minimize the risks of standing privilege across their environments. A solution like Bravura Privilege, which enables multiple types of JIT approaches, helps eliminate the need to manually manage privileged account credentials by automating key PAM processes for various use cases.
Role-Based Access Control (RBAC)
RBAC is a technique that restricts user access based on each individual's role within your organization, which is vital for protecting your most sensitive data. The Gartner maturity model survey results reveal that more than half (59%) of respondents already automate basic RBAC workflows, but they still use ad-hoc requests for additional permissions.
In contrast, 5% applied comprehensive RBAC policies to provision access across all identities, including additional ones. These organizations also used an IAM tool to handle exceptional access requests, which applied additional policies and rules for more robust governance. That's where organizations should be aiming moving forward.
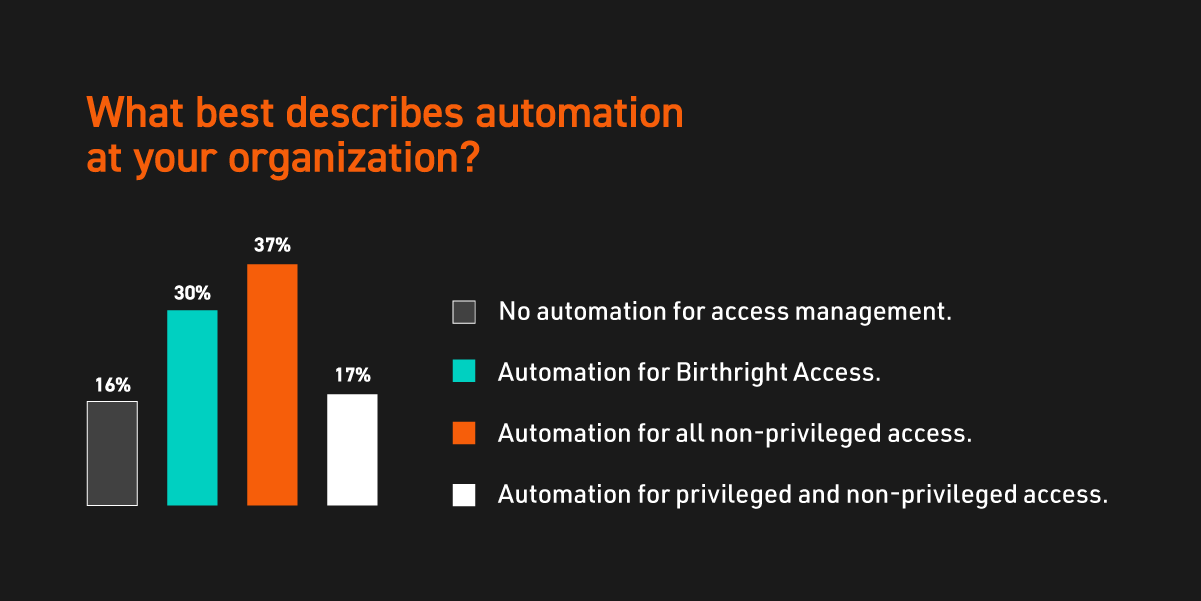
Back to topMany Businesses Automate Lifecycle Management
Life cycle management encompasses the complete IAM cycle from user creation and onboarding to final sign-on and offboarding. Automating key life cycle management processes helps streamline your IT environment and reduce risk by handling accounts you may have previously missed.
One of the most striking findings in our IAM and PAM maturity levels survey results was that the majority of respondents were split between:
- Automating basic account creation and fixing issues manually
- Using a centralized IAM tool to automate account creation and manage directories for both internal and external identities
Ideally, an organization should automate these processes using a centralized IAM tool that also manages both unsynchronized Line-Of-Business (LOB) applications. This tool should treat external identities with the same kind of rigor it applies to internal ones, possibly through a vendor management system. Only 2% of our respondents said their organizations were at this level — but it is achievable with the right systems in place.
Most Organizations Are Lagging Behind on Governance
The average governance maturity rating among our respondents was fairly low, at 2.13 out of four. Although 61% of organizations conduct partially automated access reviews on a regular basis, 32% still rely on spreadsheets and outdated tools for manual access review processes.
Our suggestion? Ditch the spreadsheets and implement an automated solution for the most effective protection against hackers.
Back to top
Take Control: Start your Identity & Privileged Access Management Self-Assessment Now
Take the reins on your cybersecurity with our quick Identity & Privileged Access Management Self-Assessment. Discover where your organization stands and learn how to close the gap between your current posture and a robust, Zero Trust-enabled future. Our assessment not only provides a clear maturity score but also outlines actionable steps to enhance your defenses against identity-targeted threats.
Don't wait for a security breach to show you the vulnerabilities in your system. By proactively evaluating and improving your identity and privileged access management strategies, you'll pave the way for a secure and resilient digital infrastructure. Start the assessment today and chart a course for cybersecurity excellence.
Download the Infographic for More Information
Want to learn more?
You can click below to download the full Gartner IAM maturity model survey results, or you can contact us to learn about how our products and services can improve your organization's IAM and PAM strategy.
Download Now