Mobile App and Access from BYOD
Bring your own device (BYOD) access to on-premises identity and access management systems without a public URL.
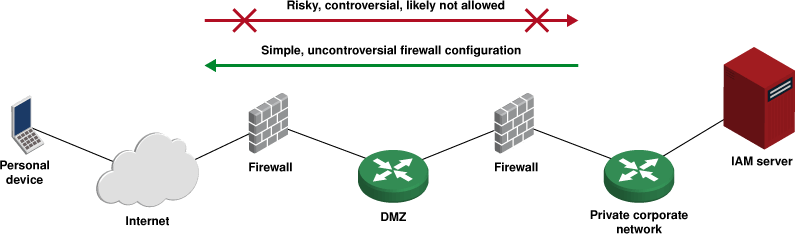
Since Bravura Security Fabric is a sensitive security application, with privileged access to other systems in an organization and/or and with access to sensitive personal data, most organizations are unwilling to expose Bravura Security Fabric directly to the public Internet (regardless of where it is hosted). This creates a problem for mobile device access to self-service, as illustrated below.
Outbound connections are routine, inbound connections are risky and rarely permitted
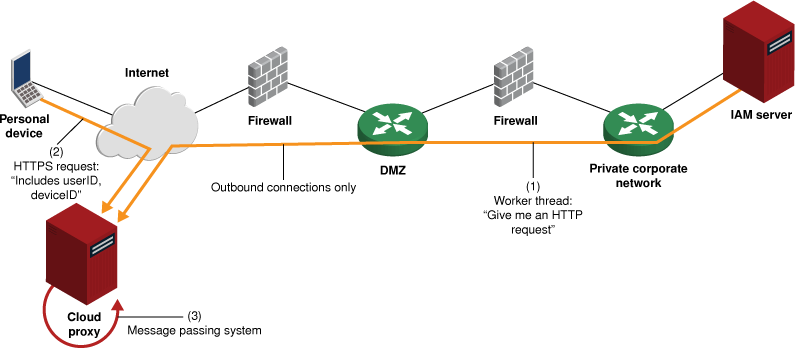
Bravura Security has developed a solution to this problem, by installing and activating an app natively on iOS and Android devices and hosting a proxy server in the cloud. This arrangement is shown below.
Using this architecture:
- An app is installed on user devices.
- Users sign into Bravura Security Fabric with their PC and ask to activate their device.
- The PC-based web UI displays an activation QR ode.
- The user runs the app on their device, which scans this QR code.
- The QR code includes encryption key material and a URL for a proxy service, in the cloud (i.e., on the public Internet).
- Users use the app to (indirectly) access the on-premises Bravura Security Fabric web portal.
- The app connects to the cloud proxy, requesting content from the on-premises portal.
- The proxy checks key material provided by the app and may discard connection attempts. In this way, connections from regular browsers or devices which have not been correctly activated for a particular Bravura Security Fabric instance are easily discarded.
- Simultaneously, a service on the Bravura Security Fabric server connects to the proxy server, asking for page requests to fulfill.
- The proxy passes requests from mobile devices to connections from the Bravura Security Fabric server.
- All connections that cross the corporate perimeter firewall in this architecture are outbound -- from the Bravura Security Fabric server to the cloud proxy.
- All connections are encrypted.